Other
- What can I do if I have run out of my bandwidth traffic?
- What can I do if my website has been flagged as an attack site?
- DotRoll webhosting security solutions
- Setup a cron job
- SSL
- Order a hosting renewal
- Creating and editing a file via SSH
What can I do if I have run out of my bandwidth traffic?
If you have received a notification email for accessing the bandwidth traffic limit, you can opt in to https://admin.dotroll.com for additional data traffic after logging in.
Steps for ordering:
- After logging in, click on Services / My Services.
- In the Actions box in the left sidebar, click the View Available Addons.
- On the page that appears, select the data bundle you want to purchase, then click Order Now.
- Then click the Checkout button and check the billing information.
- Select the form of payment and select “I have read and agree to the Terms of Service” and click Complete Order.
What can I do if my website has been flagged as an attack site?
Unfortunately we are unable to help with the reported attack site because we did not put this type of blocking on Google, but we did not. This type of blocking is useful because the visitor’s tool does not get infected, but it’s pretty uncomfortable.
To resolve this issue, follow these steps:
- For devices from which you signed in to your site, or to scan for a virus on your web site.
- Then log on to https://admin.dotroll.com and modify your hosting password as well as your FTP users’ passwords.
- If you have received a CXS notification, you can view the files in the notification email if you do not find the code code for the program code in the code then remove them. If you are using a content management system (CMS), you should definitely upgrade both the content manager and the installed add-on modules and templates.
If you have not created the website, contact the developer of the website, as we will not be able to help you with programming issues.
Google will review websites for up to 90 days, if you do not want to wait for it, you can do this by following these steps to speed up blocking.
- If the site is cleaned from harmful code sequences, please read the Google Search Console
In addition, the StopBadware site, which is http://www.stopbadware.org/ - Next, you’ll need to look at the Google Diagnostic page that you can access (at the end of the URL you want to replace): http://www.google.com/safebrowsing/diagnostic?site=http://your_domain_name.tld
Note: At the end of the URL, replace the yourn_domain_name.tld with the domain name that is experiencing the problem.
- Then, sign in to Google Webmaster Tools where you can apply for a review.
- Find it on your site with the Badware Website Clearinghouse, then click the links in the Report column to get a review of the pages by clicking the “Click to Request Review” link on the left. http://www.stopbadware.org/home/reportsearch
- If you have been granted pishing as a page, please also review the link below. http://sb.google.com/safebrowsing/report_error/
Wait for a few days, or maybe seven weeks for the systems to pass through the news of infection, and will also be able to tell you about success in Webmaster Tools.
If you have any further questions, please feel free to contact our Customer Service.
DotRoll webhosting security solutions
While developing DotRoll non-free hosting, we paid special attention to security. These security features include:
SYSTEM USERS
Unlike usual hosting solutions, security starts at the system level. Every hosting account is a system user. This allows us to run applications like Perl, Python, Ruby on Rails.
HARDENED KERNEL
Our kernel has been hardened to suit the security needs of our clients. For example, users may only see their own processes.
VIRTUAL MINI ENVIRONMENT
Every user has a very own miniature environment (chroot) in which the applications run and FTP is jailed into. This allows us to provide users with SSH access.
OUTGOING CONNECTIONS
As we reckon the need for using API’s, we have developed a solution to monitor abuse and thus allow free access to external sites to our users. PHP, for example has been fitted with all the technology we could pack into it (SOAP, XML-RPC, etc).
E-MAIL SOLUTIONS
All outgoing mail is bound to users transparently. Every user may send only from a domain belonging to that very account. Outgoing mail is digitally signed, which more and more e-mail providers recognize as a sign of trust and verifiability. Blacklists and e-mail trafic are constantly monitored so your legitimate e-mail may pass unhindered and get right where it belongs – in your user’s inboxes.
Setup a cron job
There are two options for setting.
- For the file you want to run on a file in a timely manner, at least the owner has to run the run right (0700). Also, at the beginning of the file (in the first line) you have to specify the appropriate interpreter for the file type.
For PHP file:
#!/usr/bin/php
For Shell script:
#!/bin/bash
In this case, the file should be given in the timed scripts menu in the following format: /home/username/public_html/cron.php
- Only enter the interpreter in the Timed Scripts menu before the file to run, in the following format:
For PHP file:
php /home/username/public_html/cron.php
For Shell script:
/bin/sh /home/username/public_html/file.sh
In the latter case, you do not have to configure the file for the file.
SSL
SSL / TLS is a protocol that provides secure data transfer. If supported by two endpoints of the connection, almost any other protocol can be transmitted via SSL.
An important feature of SSL is its signature. The keys can be signed and authenticated. Software vendors (such as browsers) embed embedded browsers into a list of the signatories they recognize, which are automatically accepted by the software. In other cases, the software will ask you to accept the key.
Order a hosting renewal
Follow these steps to renew:
- Log in at https://admin.dotroll.com/ with the email address you entered, when you registered your account.
- Click on the green Active icon.
- After the page loaded, below Hosting Renewals, click on Renew service for 1 year button.
Our system then draws up a billing account that allows you to extend the service immediately via credit card or PayPal.
Creating and editing a file via SSH
There are several ways to create a file through SSH. In this article, we will present the file creation with two types of word processors.
- nano – for beginner users
- vim – for advanced users
If you are editing files from a cumbersome command line, we recommend that you create a file via FTP, you can use this description below:
Create and modify a file via FTP
The following description is just an example of how to create or modify a file using SSH. Following the description, make sure you create the file at the right place. If you modify it, edit the file you want.
CREATING A FILE USING NANO
- Log in to the server on SSH.
- Navigate to the directory where you want to create or edit the file.
- Next, type the nano command and then divide by space, enter the name of the file you want to create/edit.
[server] $ nano .htaccess 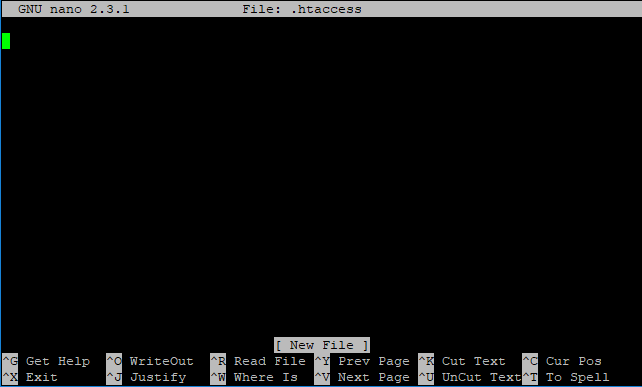
Next, start typing the contents of the file.- When you have uploaded the file with the required content, hold down the Ctrl key and press the O key (Ctrl + O).
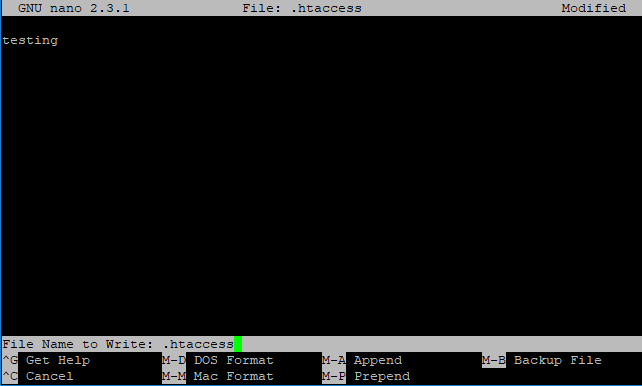
At the bottom of the screen, the editor will ask you again about the name of the file you previously specified. - You can confirm the file by pressing Enter.
- Press Ctrl+X to exit the word processor.
CREATING A FILE USING VIM
- Log in to the server on SSH.
- Navigate to the directory where you want to create or edit the file.
- Next, type the vim command, and then divide by space, enter the name of the file you want to create/edit.
[server] $ vim .htaccess 
After the word processor starts, you can upload the file by pressing the i key as it changes to INSERT mode.
- When you upload the file with the required content, use Esc to exit the insertion mode.

To save the file, type :wq, and then use the Enter key to save the file.